How to check Windows client Administrators group with Intune
The client Administrators group is a local group on Windows clients that grants administrative rights to users. This group is essential for managing Windows clients, as it allows users to install software, change system settings, and perform other administrative tasks. Sometimes, you need to grant these rights to a user, mostly developers, to install software on their own. For that, some organizations create local admin users on the clients, and the local user can use that account to install software. Mostly, this works as expected, but sometimes they use that user to grant themselves admin rights. In that case, you need to check the local admin group on the clients. Here is just one way to do that with Intune.
Intune
Because I would like to check it regularly, I have to create a remediation task in Intune. I will use a PowerShell script to check the local Administrators group on the clients. If any domain user is a member of that group but is not present in the expected list, it will show a warning in the Intune portal. I don’t want to remove the user from the group, I just want to know if there is any user who is not in the expected list, because that could block some business processes, and I would like to avoid that.
PowerShell script
Here is the PowerShell script that I will use to check the local Administrators group on the clients.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
# Define the list of allowed domain members
$allowedDomainMembers = @("DOMAIN\AllowedUser1", "DOMAIN\AllowedGroup1")
# Get the members of the local Administrators group
$localAdmins = Get-LocalGroupMember -Group "Administrators"
# Initialize a flag to indicate if any unauthorized domain members are found
$unauthorizedFound = $false
# Check each member of the local Administrators group
foreach ($member in $localAdmins) {
if ($member.PrincipalSource -eq 'ActiveDirectory' -and -not $allowedDomainMembers.Contains($member.Name)) {
$unauthorizedFound = $true
## add the unauthorized domain member to the list of bad members as array
$badMembers += "$member | "
}
}
# Return 1 if any unauthorized domain members are found, otherwise return 0
if ($unauthorizedFound) {
Write-Output "Unauthorized domain members found: $badMembers"
exit 1
} else {
exit 0
}
Save the script to a file, for example, CheckLocalAdmins.ps1.
Intune remediation script
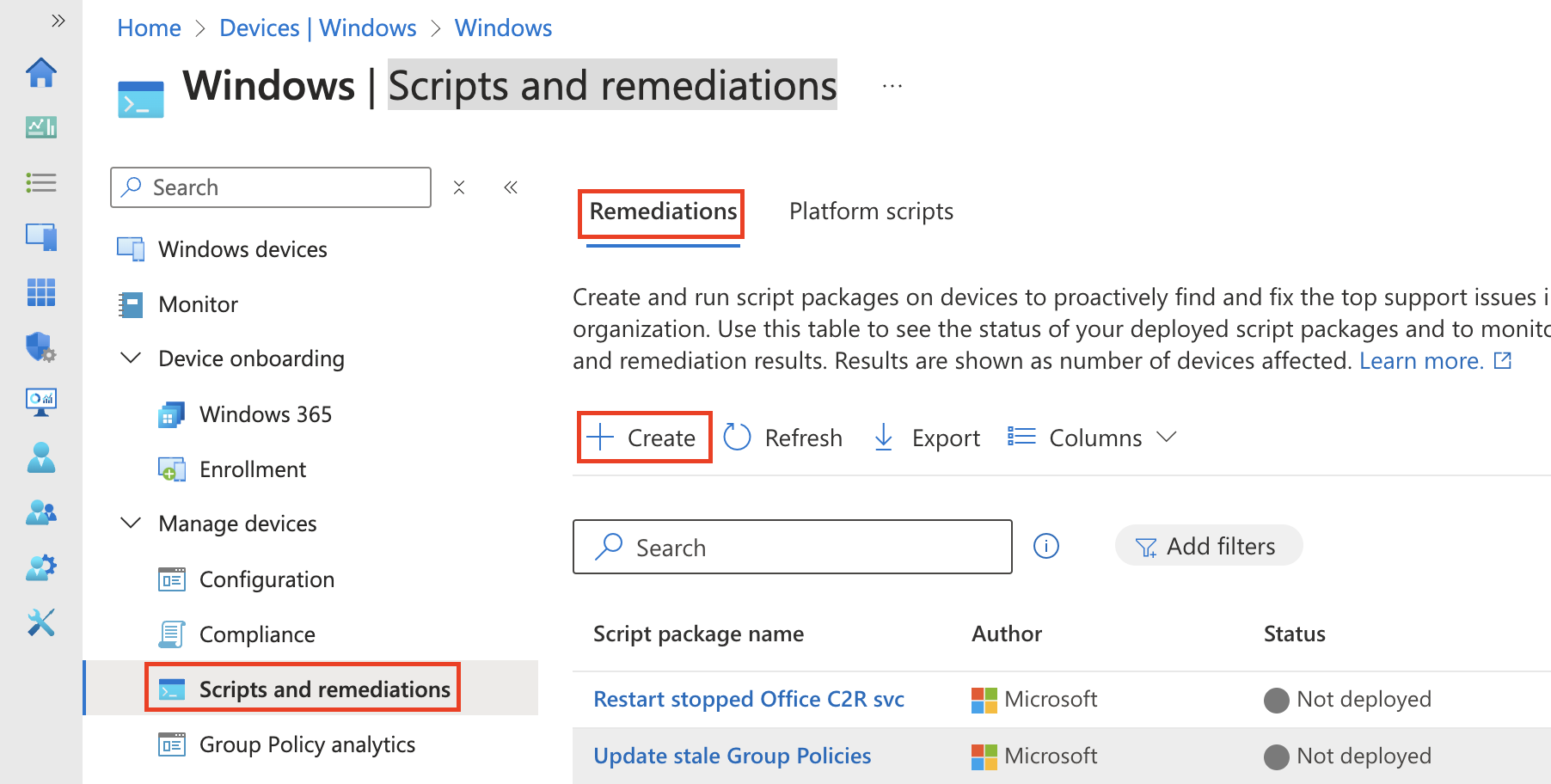
Open the Intune portal and create a new remediation script. You can find it under Devices -> Windows -> Scripts and remediations -> Create.
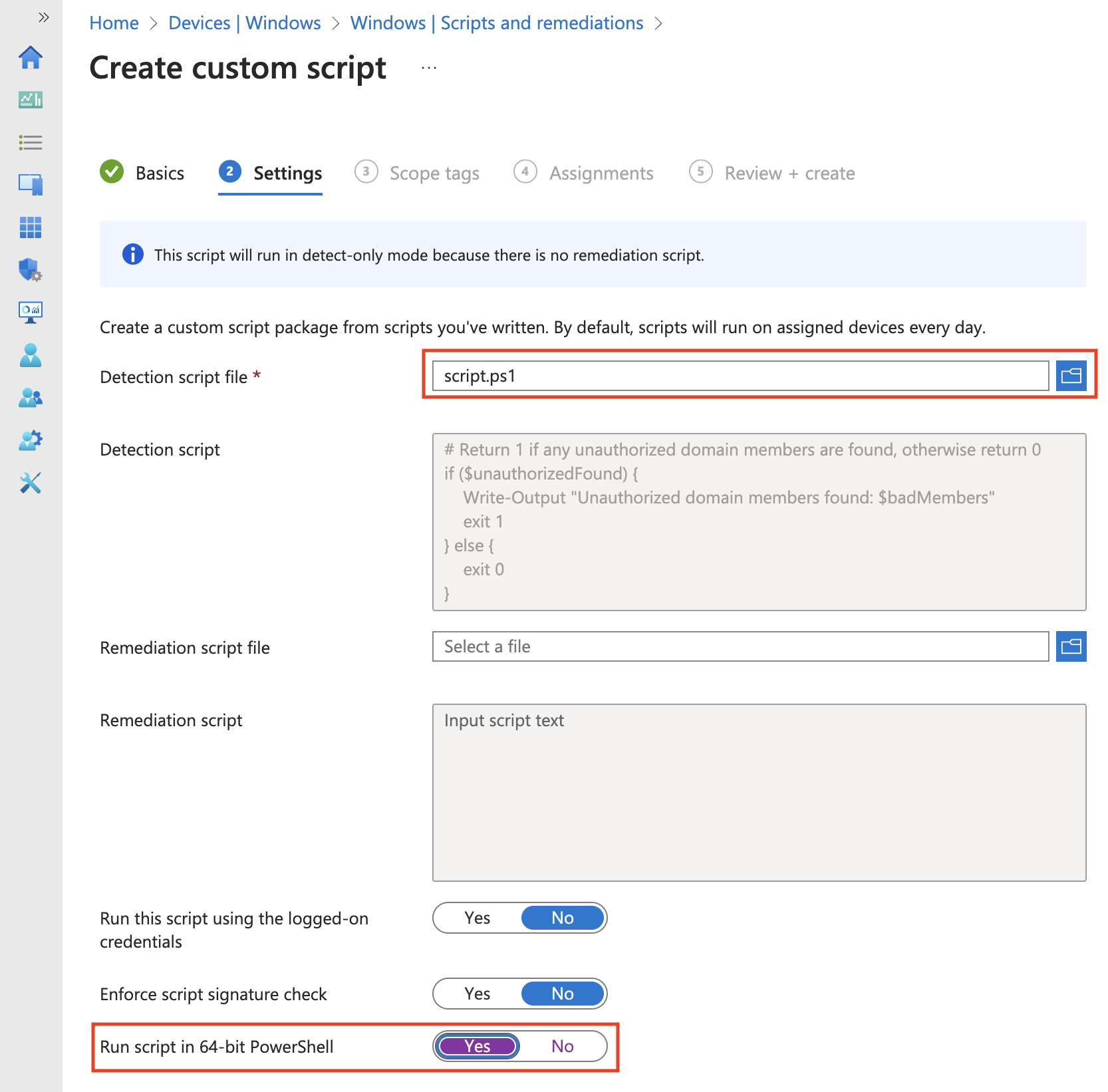
Very important to set “Run script in 64-bit PowerShell Host” to Yes, because the Get-LocalGroupMember cmdlet is only available in 64-bit PowerShell.
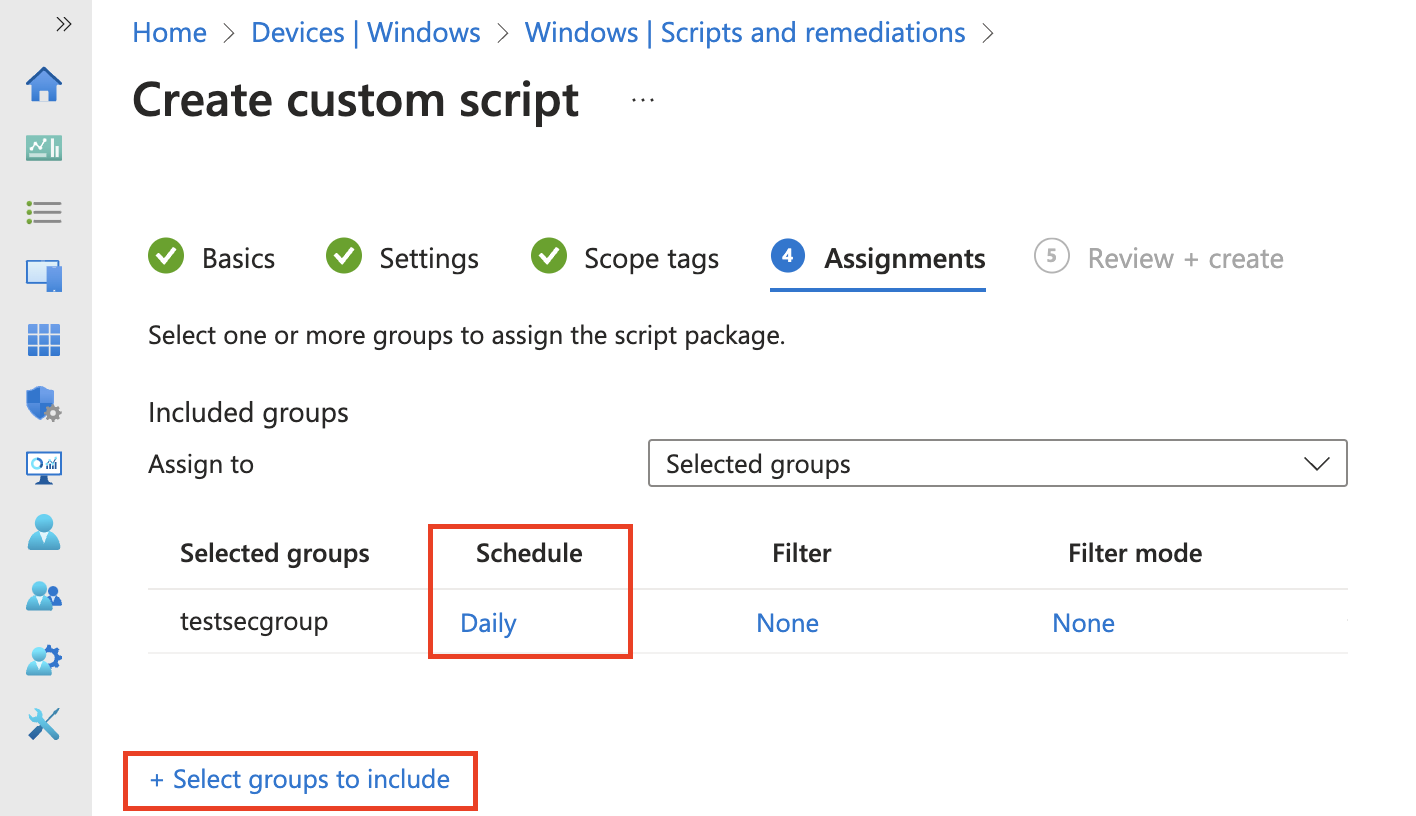
Set the script schedule to run the script regularly. Maybe every hour better to check the group.
Check the results
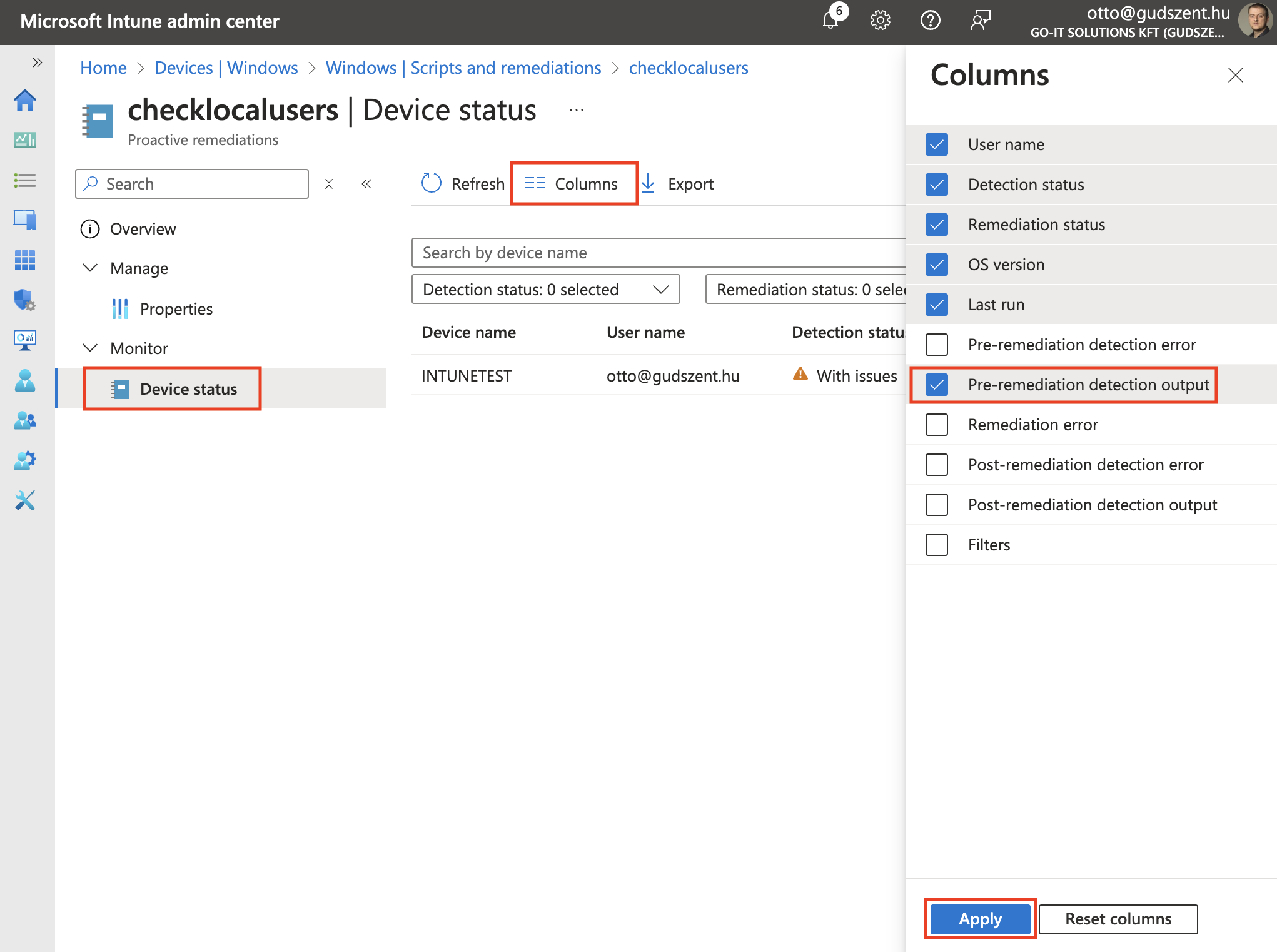
After we deployed the script to the clients, we can check the results in the Intune portal. That will take some time to get the results, but after that, we can see the results, just add the “Pre-remeidation detection output” column to the view.
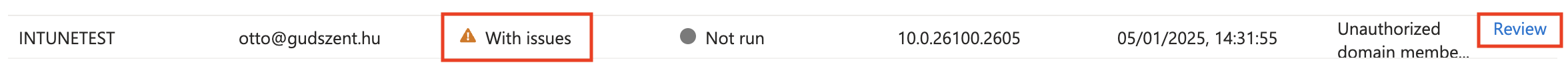
And we are done, of any unauthorized domain members are found, we will get a warning in the Intune portal and we can check it.