Global Secure Access for Private Endpoint
I just migrated my VPN from OpenVPN to Global Secure Access (GSA), so I thought I would share my experience with you. One of the most important things for me is to reach my HomeLab and Azure resources as well. Mostly, I work with enterprise customers, so a full landing zone and private endpoints are a must in my HomeLab as well. So I have to reach a few private endpoints in my Azure environment, and I wanted to reach them through GSA. For private endpoints, the key is DNS, so I had to set up the DNS properly. The regular stuff was implemented central private DNS zones, policies, and so on already but I had to send the DNS queries to GSA, and GSA needed to know how to resolve them. Not a big thing, but I wanted to share my experience with you.
Prerequisites
- Azure subscription
- Implemented proper private DNS zones and resolver
- Microsoft Entra Private Access licence, (30days trial available)
- Windows Server 2012 R2 or later
Configure connectors
We need an entry point to the network, so we need to configure the connector. Currently sadly only Windows Server is supported, so we need a windows server to run the connector resolve DNS queries and send it to the GSA. The server have to be capable to resolve the Private DNS and reach every resource what we want to reach from GSA.
In this test I want to reach my private endpoint: ‘e47e28d7-68dd-471b-adec-250e47d76731.rdweb.wvd.microsoft.com’
To be sure I checked it from that server where my connector will be installed.
1
Resolve-DnsName e47e28d7-68dd-471b-adec-250e47d76731.rdweb.wvd.microsoft.com
the result for me is:
1
2
3
4
5
6
7
8
9
Name Type TTL Section NameHost
---- ---- --- ------- --------
e47e28d7-68dd-471b-adec-250e47d76731.rdweb.wvd.microsoft.com CNAME 36 Answer e47e28d7-68dd-471b-adec-250e47d76731.rdweb.privatelink.wvd.microsoft.com
Name : e47e28d7-68dd-471b-adec-250e47d76731.rdweb.privatelink.wvd.microsoft.com
QueryType : A
TTL : 10
Section : Answer
IP4Address : 10.0.0.4
So I can resolve the private endpoint from my connector server. Important part in the DNS the ‘privatelink.wvd.microsoft.com’. Just like on-premises DNS where we have to set up the DNS forwarder, we have to do the same on the connector server. So we need to set up a DNS forwarder for the ‘privatelink.wvd.microsoft.com’ domain. But that will be little later.
Install the connector
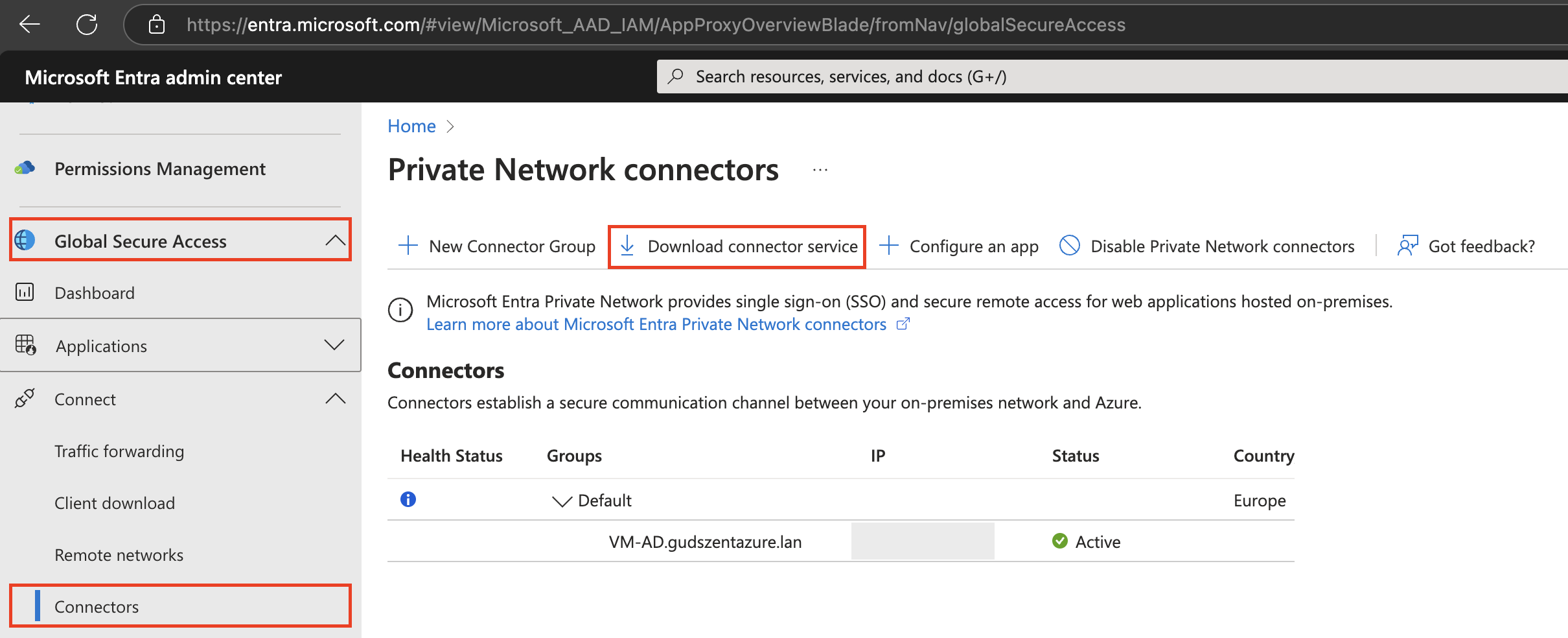
Download and install the connector from the Microsoft Entra Private Access portal.
https://entra.microsoft.com/#view/Microsoft_AAD_IAM/AppProxyOverviewBlade/fromNav/globalSecureAccess
Than install the connector on the server. Next-Next-Finish than login :)
Configure the GSA
IP range
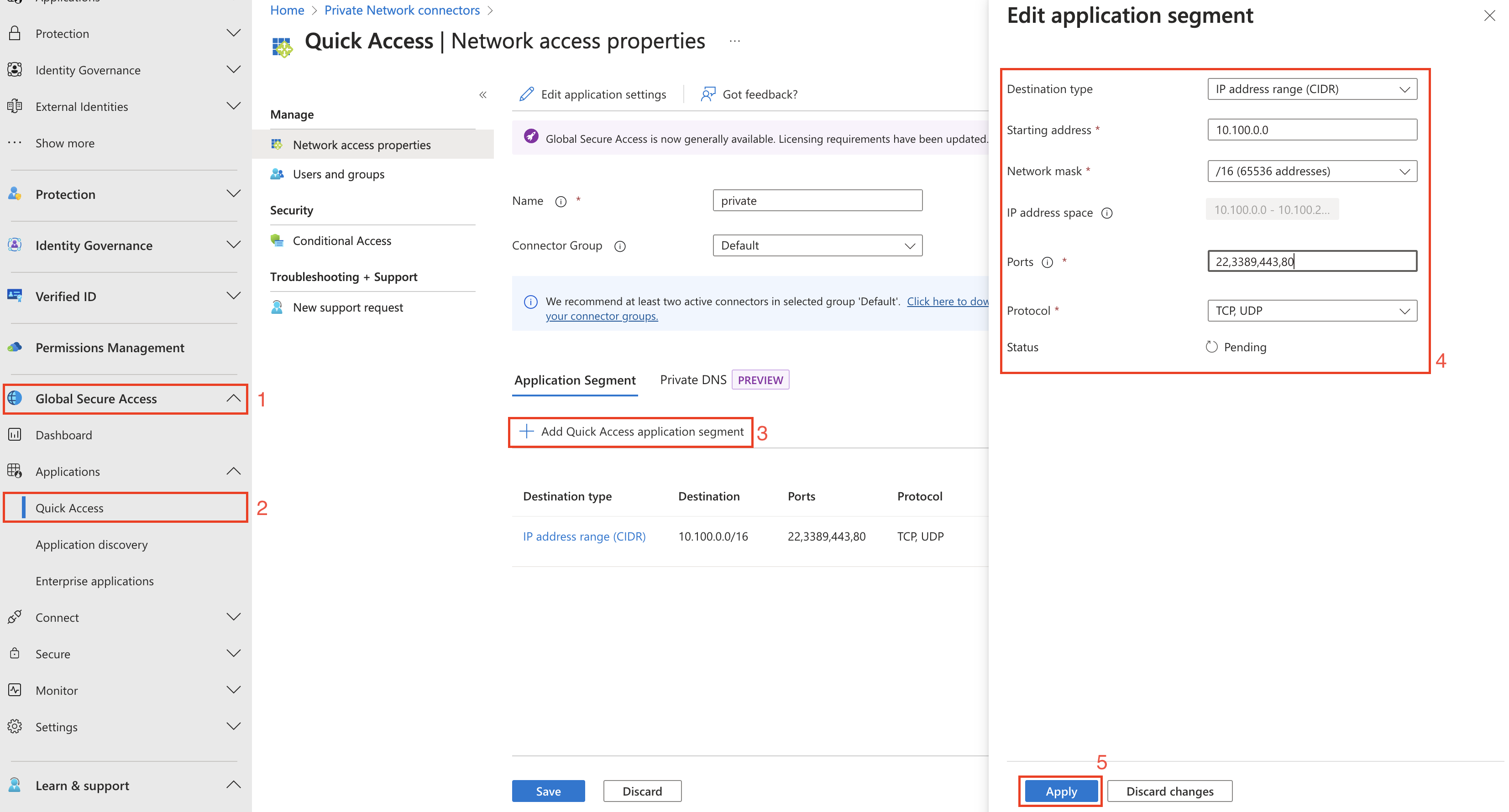
After the connector is installed, we need to configure the GSA. Go to the Microsoft Entra Private Access portal and first set the IP range. This is the range what will be reachable over the GSA. Of course the private endpoint IP address has to be in that range.
DNS Forwarder
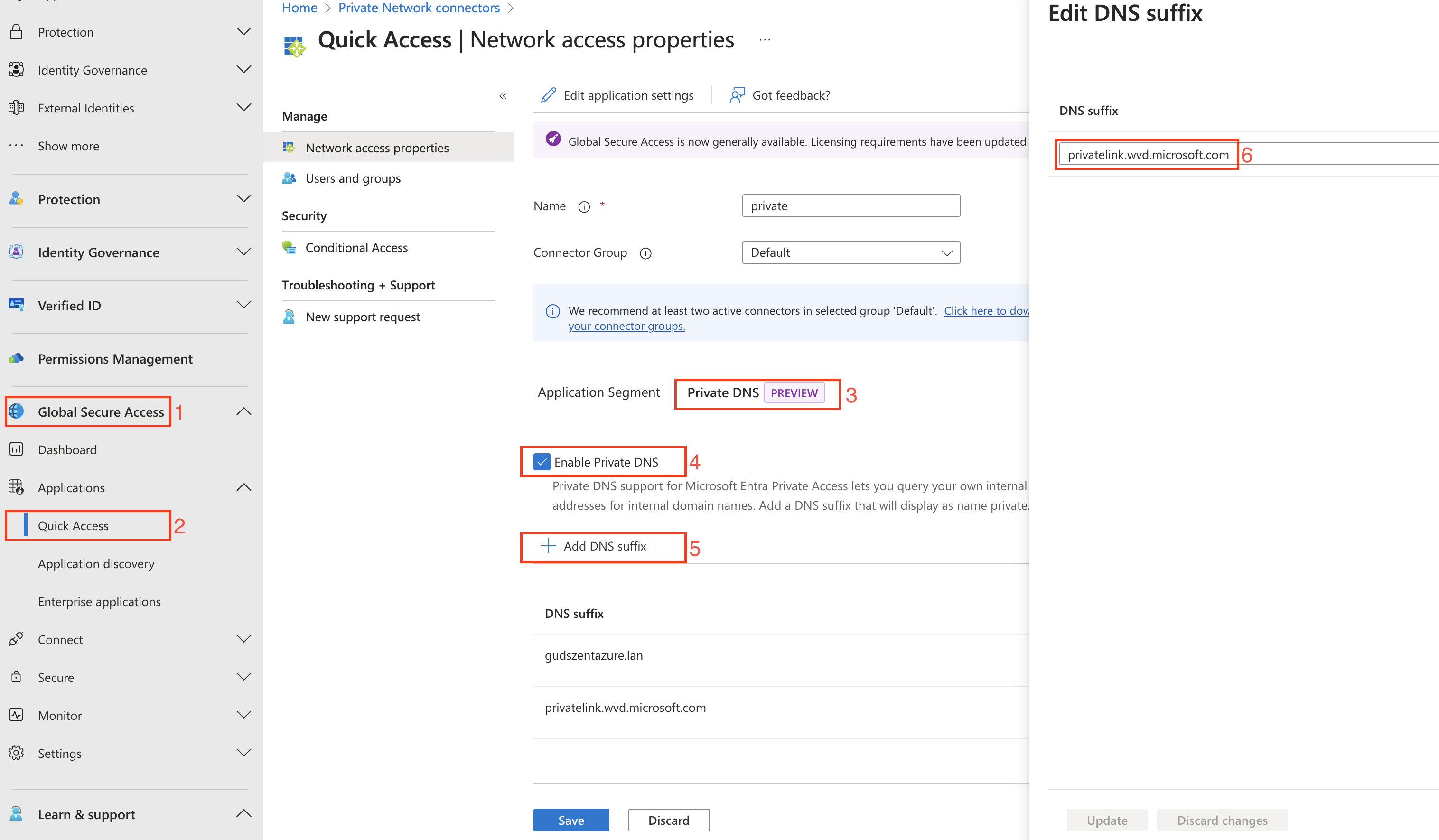
The next step is to configure the DNS forwarder. This is the part where we have to set up the DNS forwarder for the ‘privatelink.wvd.microsoft.com’ domain and all other domains what we want to resolve. First enable the feature than add the DNS suffixes.
I recommend to use the private DNS zone name, because that is the one what we will use in the connector. So in my case I added ‘privatelink.wvd.microsoft.com’.
Currently this feature is preview, so use it at your own risk.
Permissions
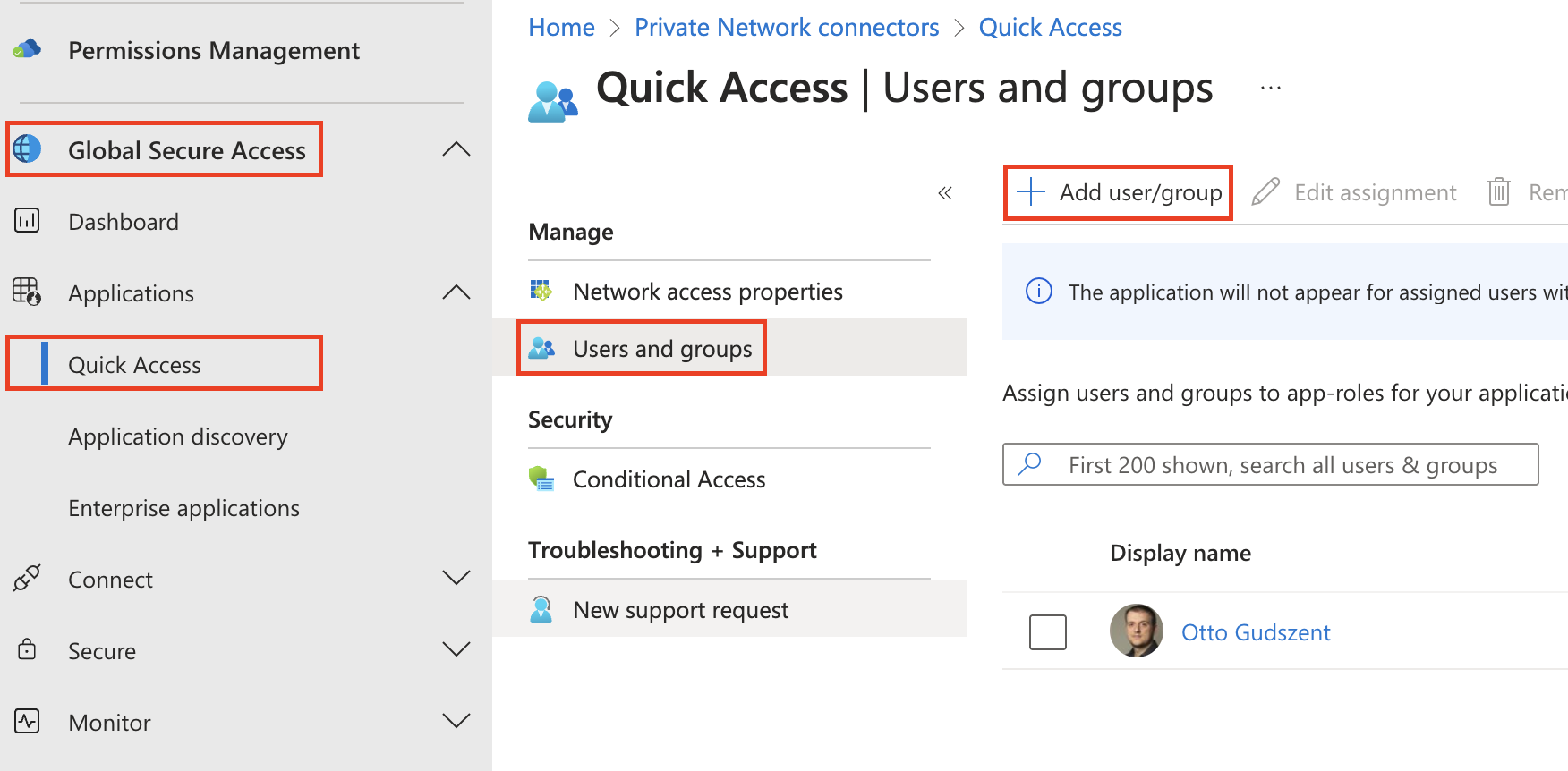
Last step add our user to the Quick Access.
Conclusion
After few days of testing I can say that this is a very good solution. I can reach my private endpoints from anywhere, and the DNS works well. The only thing what I miss is the Linux connector, but I can live with that.