Protect RDP with MFA
A simple username and password are not enough in our world. Most services, when you register there, require some kind of MFA, so why not protect RDP as well? Of course, it is always a challenge to implement some kind of 3rd party MFA solution, but if we already use some Azure services, it should be very easy :)
In this solution, I will use modern authentication to connect to an Azure VM with RDP.
Prerequisites
Usually, most companies have these, but here is the list:
- Assign users a license that includes Microsoft Entra ID P1 or P2.
- A Microsoft Entra joined machine (Entra joined or hybrid joined is good as well).
- Enable Microsoft Entra multifactor authentication with Conditional Access (Just Recommended).
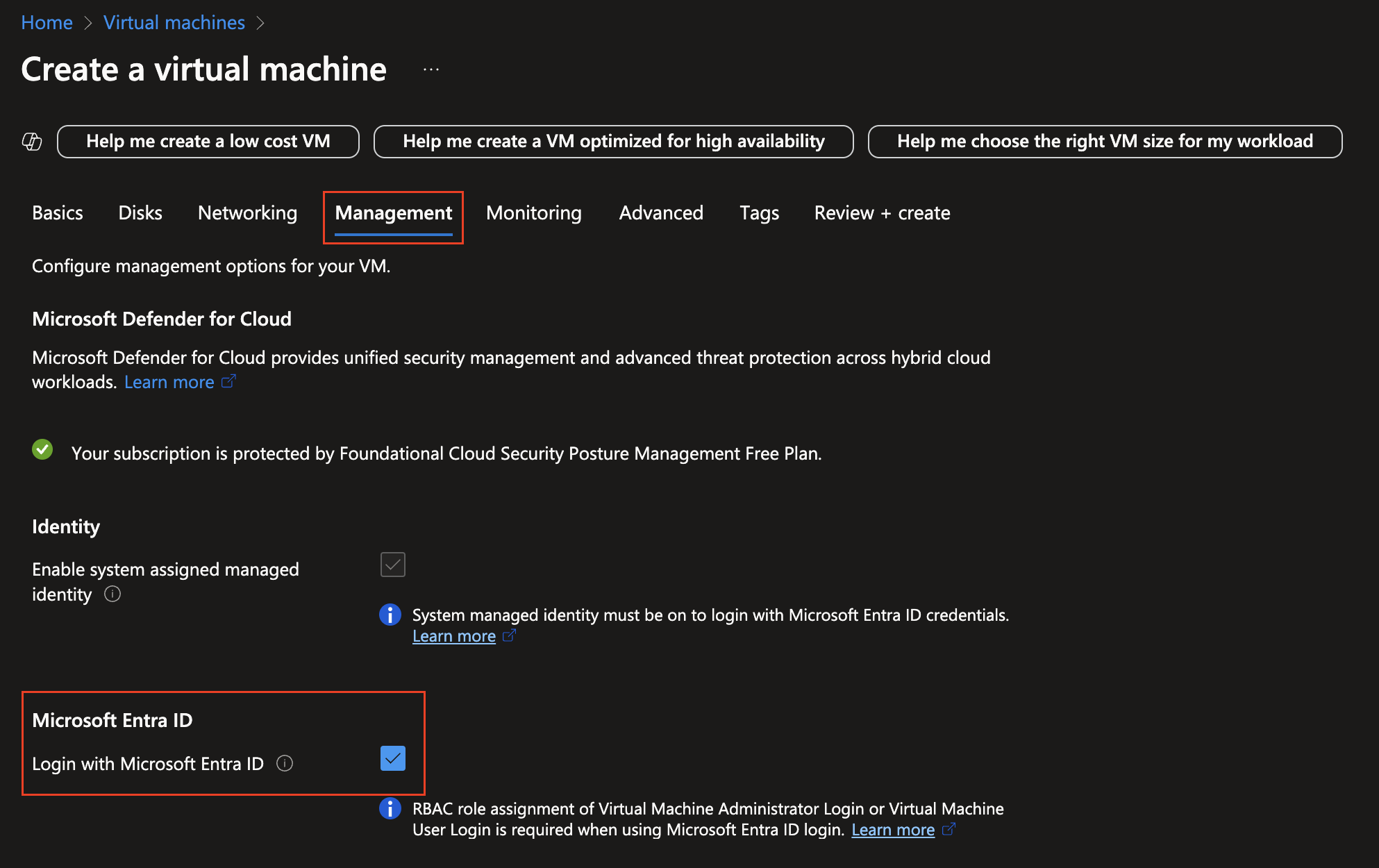
Entra Join
This solution works with Hybrid join as well. In that case, we have to sync the devices from Active Directory.
Another hand without domain join, we have to Entra join, which we can do when creating the Azure VM. Just pick these settings:
Permissions
We have two options to give users permission to log in.
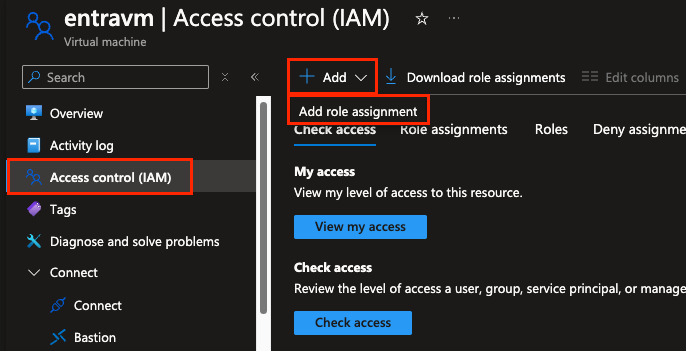
IAM
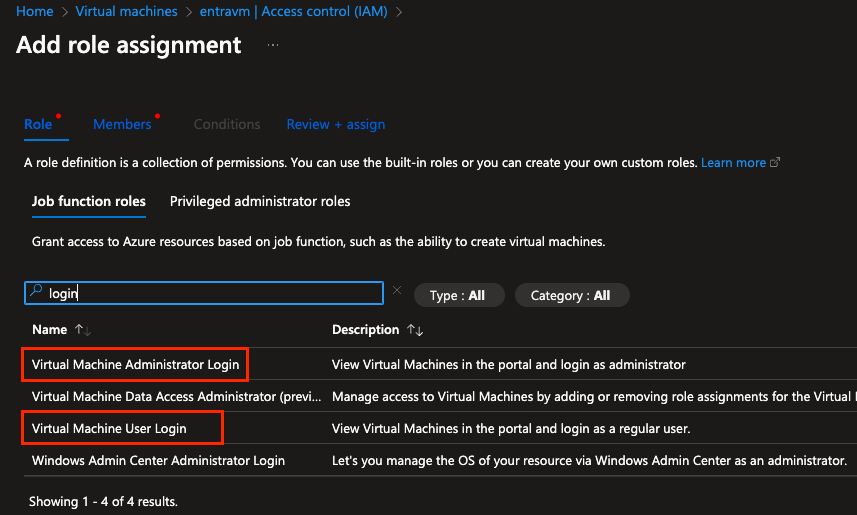
Access control (IAM) is the first solution, but it works only when we set it on the Azure VM. Go to the Azure VM. Go to the Azure VM resource, IAM and add “Virtual Machine Administrator Login” or “Virtual Machine User Login”. Yes, The Administrator role has Admin right and the user login a simple user, who does not have admin rights, but can remote login.
Local group
The second solution is to add the user to the local group on the VM. Nothing special, just add the user to the “Remote Desktop Users” group or “Administrators” group with a specific format.
1
2
3
4
# Add user to the Administrators group
net localgroup administrators AzureAD\username@domain.com /add
# Add user to the Remote Desktop Users group
net localgroup "Remote Desktop Users" AzureAD\username@domain.com /add
DNS
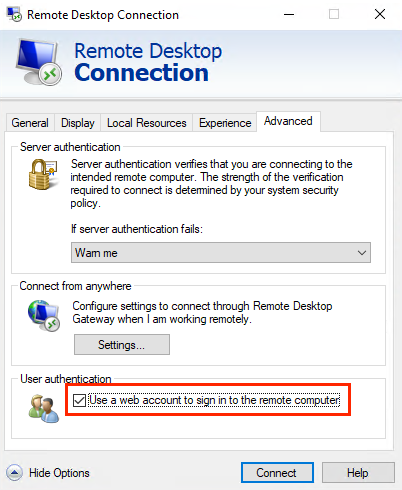
IP address cannot be used when Use a web account to sign in to the remote computer option is used. The name must match the hostname of the remote device in Microsoft Entra ID and be network addressable, resolving to the IP address of the remote device. source: Microsoft Docs
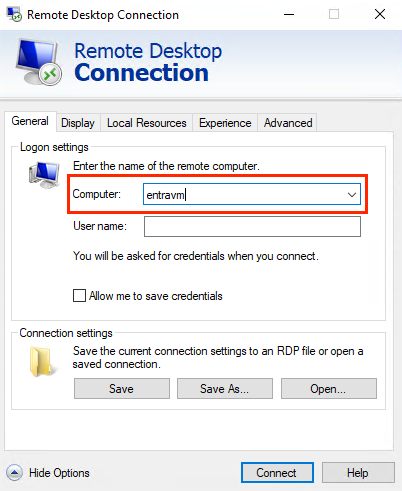
This is a very important limitation, so we have to use the hostname of the VM, and we have to use ONLY the hostname, not the FQDN. If we have a VM with the name ‘entravm.gudszentcloud.private’ we have to use only ‘entravm’ as the hostname, so the DNS server has to resolve this name to the IP address of the VM.
MFA
If your organization has configured and is using Microsoft Entra Conditional Access, your device must satisfy the Conditional Access requirements to allow connection to the remote computer. Conditional Access policies might be applied to the application Microsoft Remote Desktop (a4a365df-50f1-4397-bc59-1a1564b8bb9c) for controlled access.
source: Microsoft Docs
Connect
When we have all of these, we can connect to the VM with the RDP client.
We have to pick “Use a web account to sign in to the remote computer” and type the hostname of the VM.
So we can start the connection, if the DNS works well, the modern authentication window will appear, where we have to login and, if we setup the MFA, we have to use that as well.
Conclusion
This is a very simple solution, but very effective. Next time, I will present the Linux solution as well, so stay tuned.